I do a lot of weird things for customers, a lot of which involve email. One time I had to run some tests on gmail-sent mails. I can’t quite remember why. A problem was that my test environment was just on the LAN and my email servers were not exposed to the internet.
I figured it would be pretty simple to just configure my router to port forward to there, and then point a DNS record to my local IP. You can get cheap test domains for 99 cents for a whole year.
It turned out that my router was quite primitive/restrictive and forwarding SMTP traffic wasn’t a viable option, so I looked into option #2, ngrok, which seems like a pretty promising service to do just what I want. However, unless you pay for this, you probably won’t find it extremely useful outside of what primitive operations it supports in free mode.
Not that I don’t like supporting neat services like that, but why pay when I already have my own VPS? Option #3 was Fast Reverse Proxy (FRP), a very cool service you can run on your VPS to allow your computers to bind themselves to public domains and ports.
Here is an example checklist to setup a reverse proxy for a local email server:
(1) Install FRP on the server and configure it. Here’s my frps.ini file.
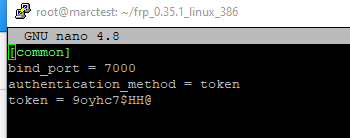
Pretty simple, right? This will listen on that port for FRP clients, and then it’s actually the client configuration that chooses what port to listen on. The token is a password for the client.
Simple startup command example:
./frps -c frps.ini
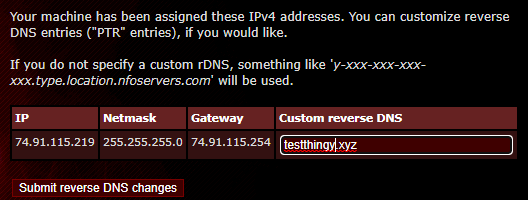
(2) Point your domain to your server.
You might also have to configure the email server to use the domain as well. For example I could buy test123.xyz for 99 cents probably, and then I can set up an MX record and A record to point to the server, so I can accept mail for addresses @test123.xyz. You might also have to set up a PTR record for the address as well. Setting that up depends on your VPS provider typically.
(3) Install the FRP client.
The client will probably get flagged by virus scanners due to the nature of it, so you probably want to download it into a folder that is already excluded by antivirus software, including Windows Defender.
Here’s a simple configuration to open port 25 on the remote machine and then forward traffic to local port 25. We’re connecting on port 7000 with the password token.
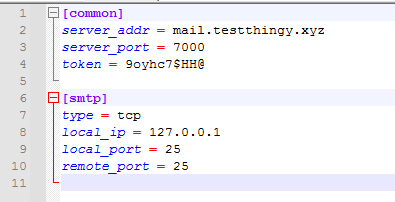
You can also dig into frpc_full.ini for a large example of the configuration flexibility, and then they also have decent instructions on their github page.
Connect the client to the server, and then you’re good to go.
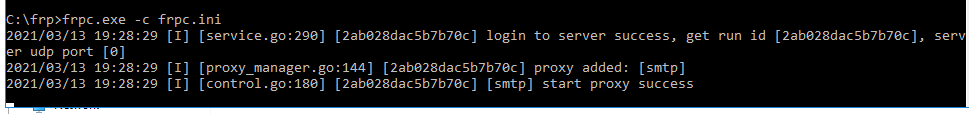
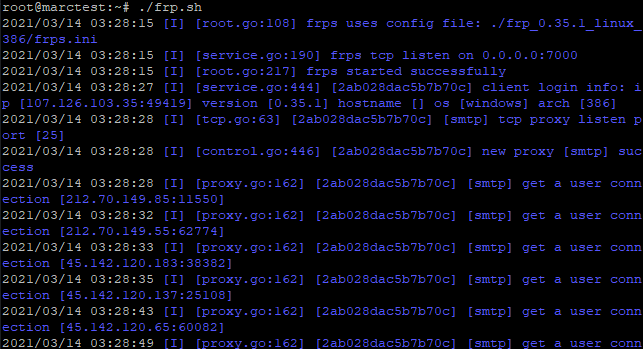
You may also note an alarming amount of connection attempts to abuse your server as soon as you open port 25. Life of a mail server.